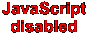
What are the chances that a hacker will guess which 2, 3, 4... 40 CORA blocs go with one another?
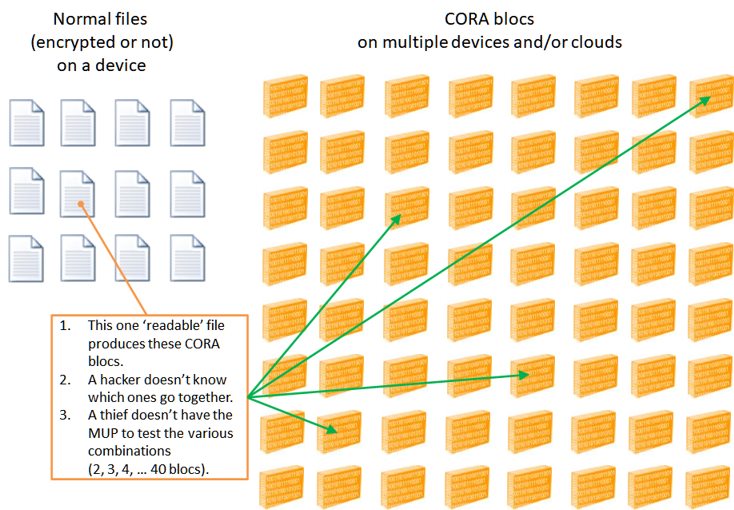
Option 1 - we don't require that the CORA blocs be entered in the proper order. The total number of combinations to test between 2 and 40 CORA blocs is only (and that is with the MUP - which should never happen):
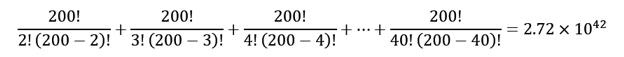
That's right, 1042 - unimaginable, and that's with only 200 CORA blocs.
Option 2 - we require the proper order - then the total # of permutations is 1.68 x 1090.